As companies grow online, they face new dangers. Malicious individuals will stop at nothing to accomplish their objectives, be it financial gain, power, or influence.
It’s crucial for businesses to prioritize cybersecurity and undertake measures like security testing to safeguard their critical digital assets from cybercriminals.
For example, in 2023, there were nearly 6 billion unauthorized data access incidents. Notably, Indian Council of Medical Research (ICMR) experienced the most significant breach of the year, compromising nearly 815 million records.
This shows that treating cybersecurity as less important won’t work anymore. It highlights how important security testing is to keep information safe.
Now, let’s talk about what is security testing, and why almost every organization needs it.
Understanding Security Testing
Security testing checks whether the software can withstand cyberattacks and how it reacts to harmful or unexpected inputs. It shows that systems and information are safe and reliable and don’t accept illegal inputs.
In cybersecurity, security testing is vital for checking and fixing security weaknesses in an application. It makes sure the application is protected from cyberattacks, unauthorized access, and data breaches.
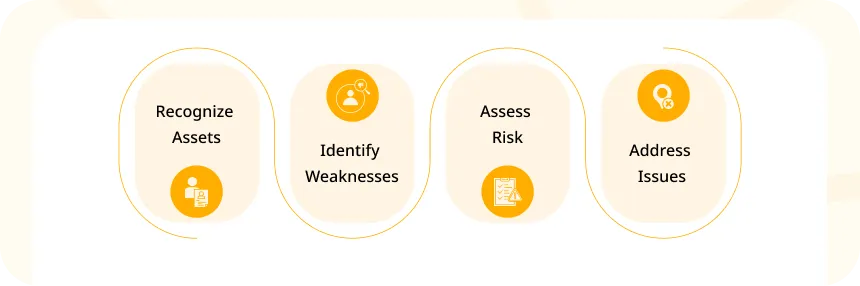
Objectives of Security Testing
- Recognize Assets: These are the important things that need safeguarding, like applications and business infrastructure.
- Identify Weaknesses: These are the actions that can harm something valuable or flaws in one or more valuable things that attackers can take advantage of.
- Assess Risk: Security testing evaluates the chance that specific threats or weaknesses might harm the organization. This is done by measuring how serious a vulnerability or threat is and how likely it is to be exploited, along with the potential consequences.
- Address Issues: Security testing goes beyond just identifying problems with assets. It provides practical guidance on fixing discovered weaknesses and can confirm that they’ve been successfully resolved.
Ensure top-notch security with ValueCoders' expert security testing services.
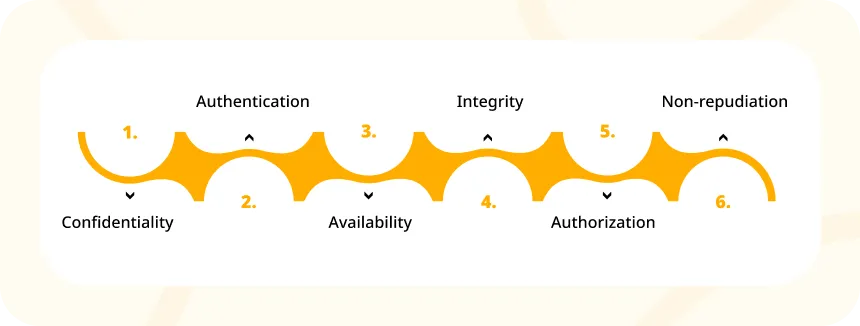
Essentials of Security Testing
Security testing makes sure that an organization’s systems, applications, and data follow these important security rules:
- Confidentiality: This means controlling who can access important information stored in a system.
- Authentication: This is the process of safeguarding important systems or data by confirming the identity of the person trying to access them.
- Availability: This makes sure that important systems or data are ready and accessible to users whenever they’re required.
- Integrity: This involves making sure that data remains reliable, accurate, and trustworthy from start to finish and can’t be changed by people who aren’t authorized.
- Authorization: This guarantees that only people with the right roles or permissions can access important systems or data.
- Non-repudiation: This guarantees that data sent or received cannot be denied later on. It’s ensured by using authentication details and a verifiable time stamp.
Security testing is crucial for strengthening digital systems against cyber threats. By following security principles and goals, organizations can improve their cybersecurity position and protect their assets efficiently.
Continuous assessment and enhancement of security measures are essential for staying ahead in the ever-changing cyber threats ecosystem.
Also read: Embracing The Future: How AI Transforms Software Testing
The Importance of Cybersecurity Testing for Businesses
A comprehensive cybersecurity testing plan examines vulnerabilities at all levels of an application. It begins with assessing the security of the application’s infrastructure and progresses to the network, database, and application layers.
Here are some of the key reasons why security testing is important for businesses to protect their website security against cyber threats:
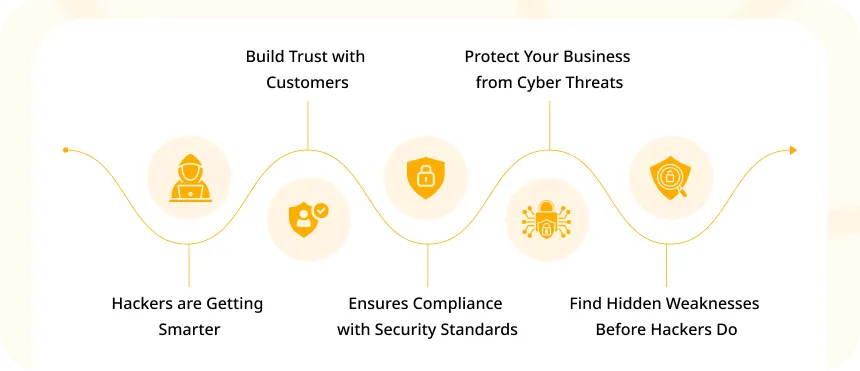
1. Hackers are Getting Smarter
As technology advances, it changes the way people live and businesses work. But unfortunately, malicious groups are also adapting these tech advancements. They’re becoming more sophisticated, posing a threat to the cybersecurity of businesses. Even though cybersecurity is improving, hackers keep finding new ways to get around it. This pushes businesses to strengthen security in their apps because that’s where most vulnerabilities can be exploited.
2. Build Trust with Customers
More and more, people are giving their important information to the companies they trust. But this also means those companies are at risk of cyberattacks. In fact, by 2025, cybercrime is forecast to cost the global economy $10.5 trillion, reflecting a 15% yearly increase. If your business doesn’t have strong cybersecurity, customers might hesitate to give you their important information. Having good app security reassures your customers that you’re taking the right steps to protect their data.
3. Ensures Compliance with Security Standards
In addition to fostering trust with customers, security testing aids your business in adhering to security regulations. Governments are rigorously enforcing laws such as HIPAA and PCI-DSS, particularly for companies that handle sensitive customer data. Integrating app security into your procedures is crucial because neglecting it can expose your business to cyberattacks. Effective security measures can also assist in avoiding fines and expenses associated with non-compliance with security standards.
Also read: How AI is Changing Software Testing Forever?
4. Protect Your Business from Cyber Threats
As technology advances, markets and industries are continually evolving. Online transactions have become prevalent, simplifying the collection of customer information. However, this also increases businesses’ susceptibility to hackers who continuously devise new methods to circumvent security measures. Hence, companies require robust security testing strategies, particularly for the applications they utilize in their operations.
5. Find Hidden Weaknesses Before Hackers Do
Identifying and resolving security gaps before attackers exploit them is vital, which is why frequent security updates are prevalent in today’s apps. Penetration testing can uncover security flaws that may have been overlooked previously. It targets the most probable vulnerabilities, assisting in prioritizing risks and utilizing resources more efficiently. You’ll gain further insight into penetration testing in the following section.
Enhance your cybersecurity posture with ValueCoders' robust security testing services.
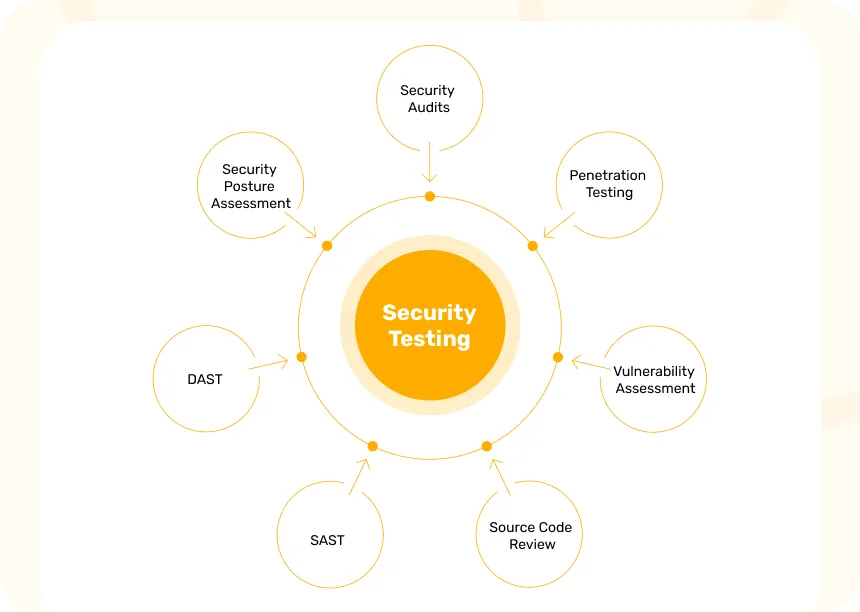
Types of Security Testing Methods
Various types of security testing employ distinct methods for identifying and addressing potential risks. By prioritizing regular security testing, businesses can monitor their security posture and make wise decisions about resource allocation.
Here are some important types of security testing that every business should know about:
1. Security Audits
Security audits involve comprehensive examinations of systems or processes to ensure they meet particular security criteria. For example, companies that process credit card transactions must conduct regular security testing to safeguard customer data, as enforced by the Payment Card Industry Data Security Standard (PCI DSS). These infrastructure security audits are essential for following industry rules. Failure to comply could result in penalties or even suspension of operations for the business.
2. Penetration Testing
What is penetration testing, also known as “pentesting,” is a systematic procedure where security experts intentionally seek and exploit vulnerabilities in an application. They assess the strength of the application’s defenses and simulate real-world attacks to determine potential outcomes if attackers were to breach them.
This method gives businesses a comprehensive insight into their security vulnerabilities, enabling them to make informed decisions about risk reduction and budget management. Security testing companies provide detailed pentest reports to businesses, outlining any vulnerabilities found in the app and recommending solutions.
3. Vulnerability Assessment
Vulnerability assessment uses automated tools to scan applications for known security problems. Some commonly used tools include Burp Suite, Mob SF, Nikto, Owasp Zap, APK tool, and Frida. Businesses can ensure that any vulnerabilities found are addressed promptly by regularly scheduling and performing these assessments. To effectively scan for the latest security flaws, it’s important to use an updated vulnerability database. Vulnerability scanners assess web applications externally to detect issues like cross-site scripting, SQL injections, command injections, insecure server configurations, and more.
4. Source Code Review
Source code review is an essential aspect of creating secure software, making it a vital type of security testing. Its goal is to uncover and address security weaknesses in an application’s source code. This proactive method ensures that security is a top priority in the software’s design, minimizing the risk of security breaches and data leaks. In a source code review, a skilled security analyst or developer meticulously examines the code, line by line, to pinpoint any security flaws, coding errors, or vulnerabilities that attackers might exploit.
5. SAST
Static Application Security Testing (SAST), also known as static analysis, is a method for testing software security through source code audit. This testing approach combines automated and manual methods to find vulnerabilities. It’s useful because it can detect problems without needing to run the software in a live environment. Engineers can carefully review the software source code audit and systematically address any security issues they find. SAST tools can delve deep into the code, uncovering vulnerabilities that might be missed by manual inspection.
Also read: Cybersecurity In Software Development: Why It Matters More Than Ever
6. DAST
Dynamic Application Security Testing (DAST) examines an application from the frontend to identify vulnerabilities using simulated attacks. This automated method is best suited for internal-facing, low-risk applications that need to meet security regulations. For medium-risk applications and critical apps with minor changes, it’s best to use a combination of DAST and manual web security testing to check for common vulnerabilities. This approach simulates real-world attack scenarios and provides valuable insights into potential weaknesses from an external viewpoint.
7. Security Posture Assessment
A security posture assessment combines security scans, ethical hacking, and risk evaluation to analyze a company’s overall security stance. This assessment combines aspects from various security testing methods, enabling businesses to create a comprehensive security strategy. Here are some reasons why your business might conduct a cybersecurity posture assessment:
- When you want to fully assess your current cybersecurity status.
- When you need to confirm that required cybersecurity measures are correctly in place.
- When you require a thorough analysis of vulnerabilities.
- When you’re undergoing ongoing technology integration projects or making changes to your technology setup.
Methods of Testing Application Security
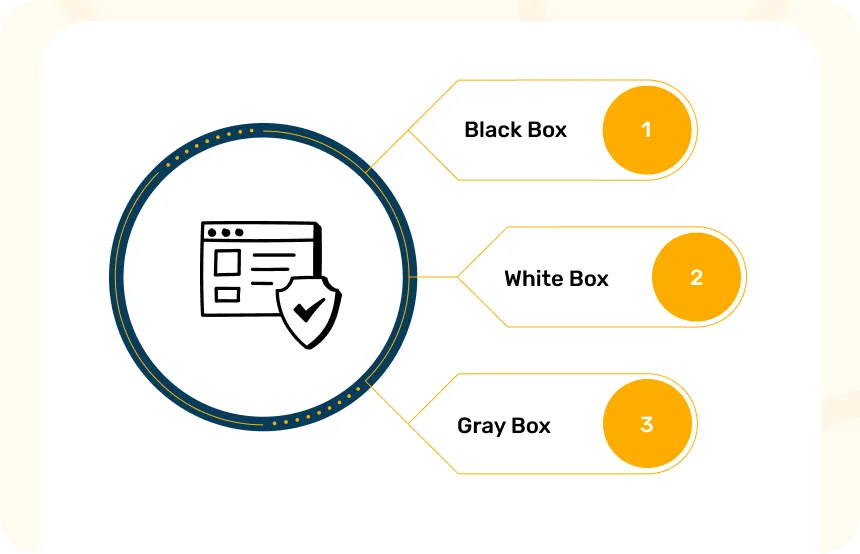
External companies provide three types of approaches to security testing. These are:
- Black Box: Black-box testing looks at the outward features and behavior of the software. It checks how an application is supposed to work from the user’s point of view.
- White Box: This type of testing is done from the developer’s viewpoint. It’s also known as glass box testing, transparent box testing, structural testing, or non-functional testing.
- Gray Box: Gray Box Testing combines elements of both Black Box and White Box Testing in software testing for business. It uses program inputs and outputs, while also considering code information when designing tests.
Security testing companies typically recommend Gray Box testing for businesses because it’s efficient and produces effective results.
Let ValueCoders fortify your digital assets with our advanced security testing solutions.
Performing Security Testing on Applications
There are two primary methods for testing application security: manual testing and automated testing. Security testing is conducted on web, mobile, and cloud applications, as well as API and IoT devices.
Both approaches have advantages, and they are frequently combined to ensure comprehensive testing. Here’s what you should understand:
1. Manual Testing
Manual testing depends on human knowledge and intuition to discover vulnerabilities that automated methods might overlook.
Testers mimic user actions on the website, attempting to exploit vulnerabilities by altering input fields, cookies, and HTTP requests.
Manual testing demands a deep understanding of application security testing and is both laborious and time-consuming. Nonetheless, it can reveal intricate vulnerabilities that automated tools may miss.
Benefits of Manual Security Penetration Testing:
- Tests all security levels of the target application thoroughly.
- Utilizes the tester’s knowledge, expertise, and skills.
- Overcomes the limitations of automated vulnerability scanners.
- Uses multiple tools for a comprehensive examination.
- Essential for a thorough security assessment.
- Provides a detailed overview of all security issues in the target software.
2. Automated Testing
Automated testing involves using software tools to automatically scan a website for vulnerabilities and flaws. These tools can quickly identify common vulnerabilities, saving time and effort during testing. However, they may also generate false positives or miss complex vulnerabilities that require manual testing.
Benefits of Automated Security Penetration Testing:
- Rapid testing and prompt delivery of results, preventing delays in the staging process.
- Conducts frequent vulnerability scans to detect new vulnerabilities quickly.
- Doesn’t require physical effort during testing.
- Capable of gathering extensive data across networks.
Challenges in Conducting Security Testing
There’s no doubt that security penetration testing is valuable for assessing an IT system’s security. Despite its importance, many security teams struggle to make pen testing effective in their organization.
What are the biggest challenges businesses face when preparing for an upcoming pen test? Read on to find out:
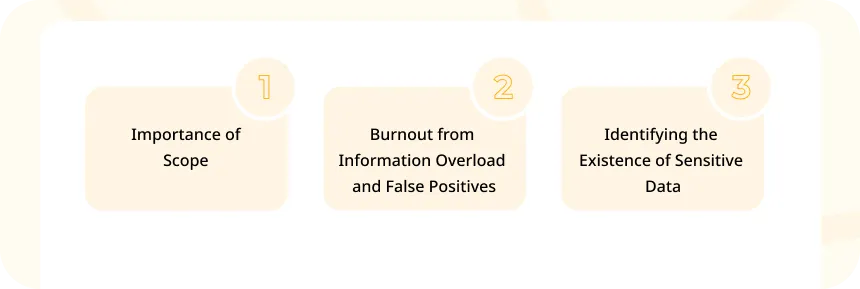
1. Importance of Scope
Defining the scope is important for the success of the procedure. With numerous items and testing methods, setting clear boundaries can be challenging. Scope creep can happen due to too many options and differing views on priorities. A broad scope that tries to cover everything may lead to less meaningful results, as pen testers often can’t perform in-depth evaluations on all areas.
2. Burnout from Information Overload and False Positives
Security professionals constantly receive alerts, which can be overwhelming. They spend a lot of time sorting through these alerts, with more than 50% being false positives. This can lead to burnout.
- 70% of security professionals evaluate more than ten alerts daily, and 78% spend over 10 minutes on each one.
- 83% of security testing staff have experienced alert fatigue.
3. Identifying the Existence of Sensitive Data
Securing sensitive data is a common concern for many businesses, regardless of their size. However, the first step is to identify the sensitive data they have.
As per a study, 67% of survey respondents find identifying where sensitive data is in their organization to be their most challenging task.
Safeguard your digital assets with ValueCoders' comprehensive security testing services.
Effective Strategies for Conducting Security Testing
Ensuring robust cybersecurity requires following established protocols and standards. Maintain the site security checklist and recommended practices for effective security testing:
-
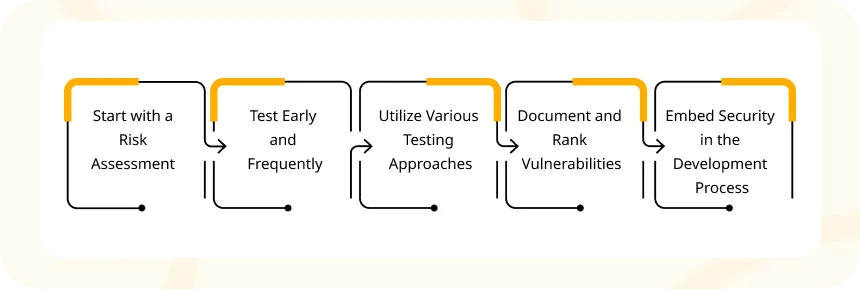
Start with a Risk Assessment
Prior to conducting security testing, it’s crucial to evaluate the risks linked to the system under examination. This process aids in pinpointing the system areas requiring the most attention, ensuring testing efforts concentrate on the most critical aspects.
-
Test Early and Frequently
Begin security testing early in the development process and maintain it throughout the various stages. This approach enables the early detection of vulnerabilities when they are simpler and less costly to rectify, minimizing the risk of introducing errors later in the development process.
-
Utilize Various Testing Approaches
To conduct comprehensive security testing, it’s essential to utilize a combination of automated scanning tools, manual penetration testing, and code reviews. Each method has its advantages and disadvantages, so blending them together allows for a more extensive exploration of vulnerabilities.
-
Document and Rank Vulnerabilities
Once vulnerabilities are identified, it’s crucial to document and prioritize them according to their severity and the likelihood of exploitation. This ensures that vulnerabilities are promptly and effectively addressed. It’s essential not to overlook or downgrade potential vulnerabilities after discovering them.
-
Embed Security in the Development Process
Successful security penetration testing goes beyond testing the system after it’s built. It should be incorporated into the development process from the outset. This involves adhering to secure coding practices, conducting frequent code reviews, and integrating security testing into the continuous integration and delivery process.
Also read: A Guide To Security In Software Development – White Paper
Choose ValueCoders for Security Testing Service
While automated and Artificial Intelligence (AI)-driven application security testing solutions offer notable benefits, they also have their limitations.
Automated testing often misses hard-to-find vulnerabilities that malicious actors exploit, has limited language support, and tends to produce numerous false positives, which can frustrate skilled developers and security professionals.
Trust ValueCoders for reliable security testing solutions tailored to your needs.
Our security testing services protect businesses in different industries from cyber threats, enhancing their reputation and maintaining customer loyalty.
ValueCoders addresses these challenges by providing a proactive security testing approach, utilizing insights from a team of ethical hackers committed to outsmarting attackers on your behalf.
- We are a top security testing company and create a detailed report of your application.
- Our ethical hackers provide insights to map your assets, offering complete visibility and control.
- We pinpoint and prioritize the most critical issues in your app, testing them from an adversarial viewpoint to uncover the vulnerabilities that cybercriminals are likely to exploit.
- Our pentest report assists in achieving regulatory compliance testing with HIPAA, PCI DSS, SOC 2, ISO 27001, and GDPR.
Moreover, partnering with ValueCoders guarantees a strong digital presence and investment in a future where your application thrives, clients trust you completely, and your business grows rapidly.
Don’t hesitate! Secure your digital future with ValueCoders’ expertise, and let’s embark on a journey of trust, quality, and development together. Contact us today!