Increasing digitization has made software development a crucial part of modern businesses, increasing the risk of cyberattacks. Therefore, hiring software developers to protect your software is essential, as they store users’ confidential or sensitive financial and personal information.
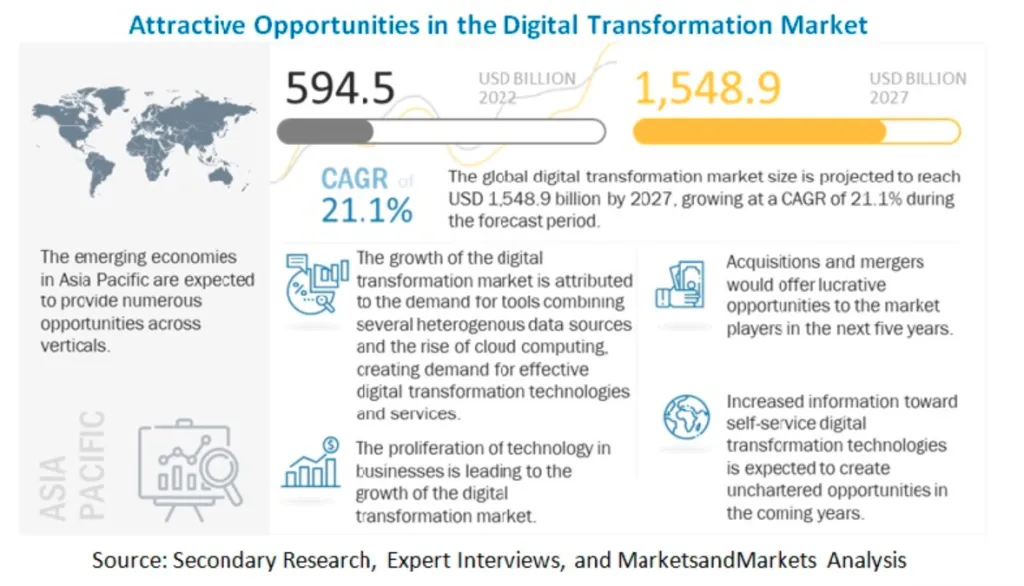
The platform Markets and Markets estimated the digital transformation market to be worth USD 594.5 Billion in 2022 and USD 1,548.9 Billion by 2027, growing at a CAGR of 21.2%.
In this blog post, we’ll discuss the increased significance of cybersecurity in software development and the need for companies and developers to adopt a diligent security strategy.
We will also thoroughly review the current status of software security and the steps you can take to protect your users’ information, covering everything from the most typical types of cyberattacks to recommended practices for protecting your app.
Also Read: A Guide To Security In Software Development {Whitepaper}
Importance of Cyber security in Software Development
Building secure software solutions, one code at a time - with ValueCoders
The following points sum up the importance of cybersecurity in software development:
Protecting User Data
Cybersecurity is essential for preventing the theft or unauthorized access of sensitive data, including financial information, user data, and personal information. Mobile apps are a prime target for cyberattacks because they gather and retain copious amounts of personal information. By putting strong security measures in place, software developers can prevent this data from being stolen or accessed without permission.
Maintaining Customer Trust
Clients give their personal and financial information to mobile software, and a security lapse can swiftly undermine that trust. Software developers can achieve the security of their client’s data and maintain their confidence by prioritizing cybersecurity. Customers are more likely to stick around and refer a mobile app to others if they feel confident using it, which can aid in the app’s long-term growth and success.
Compliance with Regulations
Sensitive information must be stored and transmitted securely as per laws like GDPR, HIPAA, and PCI-DSS, which apply to many businesses. These rules carry hefty financial consequences for noncompliance. Software developers can ensure their apps comply with these laws and prevent potential legal and financial repercussions by prioritizing cybersecurity.
Prevention of Financial Losses
A security breach can lead to the theft of sensitive information and financial losses for the affected people and the firm. Software developers can help stop these losses by giving cybersecurity priority. It is critical to give cybersecurity priority right away because, in a breach, the expense of reestablishing security and fixing damage may be significant.
Also Read: Streamlining Finance: The Benefits Of AI And ML In Fintech
Maintaining Brand Reputation
Restoring a company’s reputation after a security breach can be challenging and expensive. Software developers may protect their brand’s reputation and avert potential harm to their business by placing cybersecurity as a top priority. A software can stand out in a competitive market and draw more users with a reputation for security and dependability.
In this informative video, we explore the significance of cyber security in software development and its impact on businesses and organizations.
3. Biggest Threats to Software Security
Cyberattacks can take many forms, from straightforward hacking efforts to trickier phishing schemes. Companies should Hire Software Developers to protect and ensure secure software development. Some of the most typical attack types are:
Malware
Malware is software explicitly created to damage a device or steal private data as malware. An infected machine is used to carry out this kind of attack, which might cause data loss or theft by infecting it with a malicious program. Businesses should consider expert software development services to protect their apps from such threats.
MITM (Man-in-the-middle attacks)
It may alter the conversations between two parties by a third party who overhears them. For example, an attack known as a man-in-the-middle could happen if you try to carry out a secure transaction over a public Wi-Fi network.
Attackers can intercept user and server communications, change the data being sent, and steal sensitive data. Protecting sensitive data by partnering with a reputed Software Development Company that ensures software security is essential.
Unsecured Wi-Fi Networks
Public Wi-Fi networks are frequently unprotected, making them open targets for hacker attacks. Users who join these networks risk having their private and financial information hacked. Therefore, using a virtual private network (VPN) or avoiding public Wi-Fi networks for critical transactions is advised.
A successful cyberattack may steal sensitive information and destroy data. Therefore, it is crucial that custom Software Development Services and developers have a proactive security strategy and put protective measures in place to guard against these kinds of assaults.
Building secure software solutions, one code at a time - with ValueCoders
4. Best Practices for Software Security
Several crucial practices can protect your software from cyberattacks. The most successful techniques are:
Encryption
Encryption transforms private information into a form that can communicate securely over the internet. In the automotive software development sector, encryption is especially critical for protecting vehicle data, such as driving patterns, location tracking, and connected services, from unauthorized access. Additionally, for applications incorporating computer vision software development, securing visual data through encryption ensures that sensitive images and video feeds are protected from cyber threats.
Security Assessments
A crucial step in protecting the security of your application is to conduct regular security evaluations. The software is rigorously tested in these evaluations to find any potential security concerns or flaws. Besides ensuring that your app is secure for your users, this enables you to address any concerns before they become bigger.
Regular Software Updates
Updating your app’s software is crucial for preserving software security. It helps with the most recent security measures and correct known security flaws. To protect your software applications against the most recent attacks, keeping the software updated is critical.
Balancing User Experience and Security
We must balance the user experience and security while software developers create their applications. On the one hand, adding extra steps or making your app more difficult to use can cause security measures, making your app less user-friendly.
Conversely, your app may be vulnerable to cyber-attacks if security measures aren’t taken care of. Finding the right balance between a secure software environment and a satisfying user experience is essential.
The Future of Software Security
With new technology and trends appearing regularly, the security of software apps is continuously changing. According to Mordor Intelligence, the IoT market’s global Artificial Intelligence (AI) is expected to grow at a CAGR of 27.86% from 2018 to 2028.
The following are some of the major themes that will affect how to secure mobile applications in the future:
Artificial Intelligence and Machine Learning
Software security could drastically change due to advances in artificial intelligence and machine learning. These innovations make it feasible for security systems to identify trends, learn from data, and detect potential threats more quickly and efficiently. Because identifying and resolving security issues is automated, it will be easier to maintain the security of your app.
Also Read: What Is The Role Of Artificial Intelligence In The Financial Sector?
Internet of Things (IoT)
The term “Internet of Things” (IoT) describes a network of increasingly interconnected items, such as wearables, smartphones, household appliances, and other gadgets. The significance of software security for these devices is growing as the number of linked devices expands.
IoT devices could be targets for cyberattacks, and if they are not adequately secured, they could jeopardize the safety of the data they gather and communicate. An increasing emphasis on protecting IoT devices from threats and securing them will be made to solve this.
Conclusion
To conclude, the importance of cybersecurity in software development cannot be overstate d. With the increasing cyberattacks, companies, and software developers must proactively secure their apps and protect critical data.
ValueCoders ensures two vital practices that can help lower the danger of cyberattacks encrypting data and regularly upgrading software. With new technology and trends appearing regularly, software security is continuously changing.
We ensure to update your software with the most recent security method to protect your software from potential dangers. Making a cybersecurity investment is crucial to guarantee your mobile app’s stability and long-term profitability.